Ukraine Tracks a Record Number of Cyber Incidents During War
Data Breach Today
NOVEMBER 16, 2023
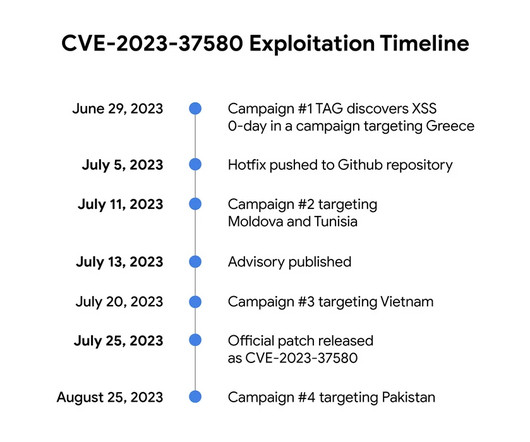
Hackers Steal CCTV Footage to Study Efficacy of Missile Strikes and Drone Attacks Ukraine's national computer emergency response team, CERT-UA, says it sees an increase in cyber incidents as Russia's invasion continues. While wiper attacks are ongoing, a rising Russian hacker tactic involves stealing private CCTV footage to study the efficacy of missile strikes and drone attacks.









































Let's personalize your content