3CX voice and video conferencing software victim of a supply chain attack
Security Affairs
MARCH 30, 2023
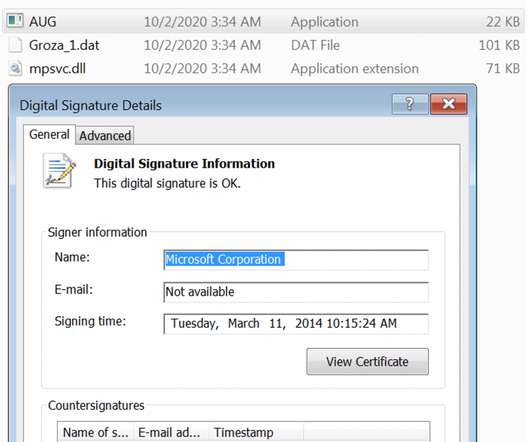
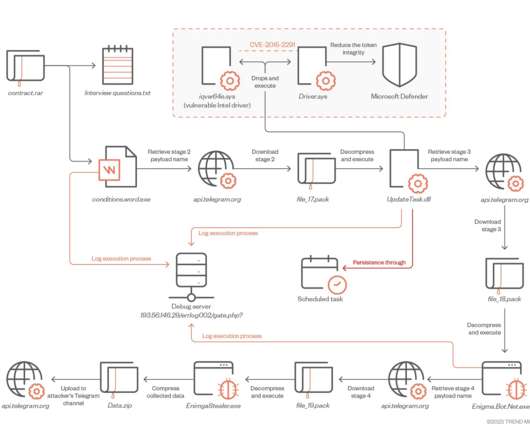
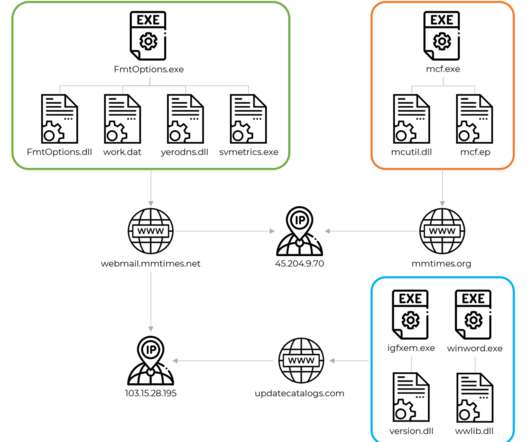
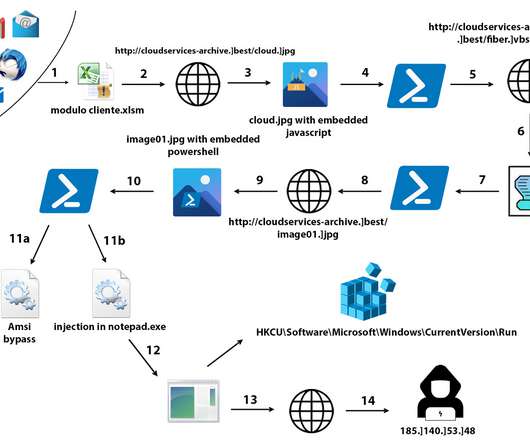
The company started distributing digitally signed Trojanized installers to its customers “The trojanized 3CXDesktopApp is the first stage in a multi-stage attack chain that pulls ICO files appended with base64 data from Github and ultimately leads to a 3rd stage infostealer DLL still being analyzed as of the time of writing.”






















Let's personalize your content