China-linked LuminousMoth APT targets entities from Southeast Asia
Security Affairs
JULY 14, 2021
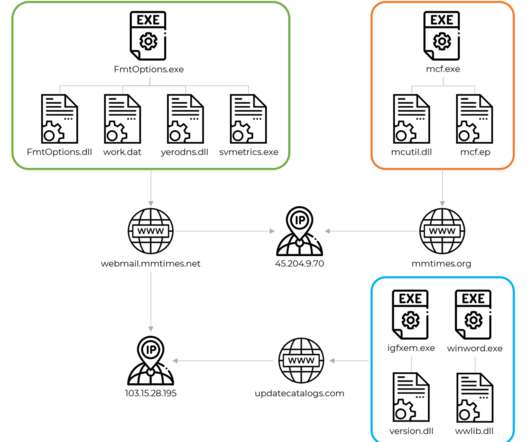
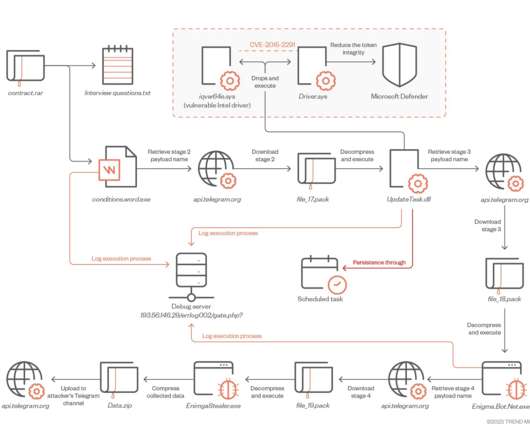
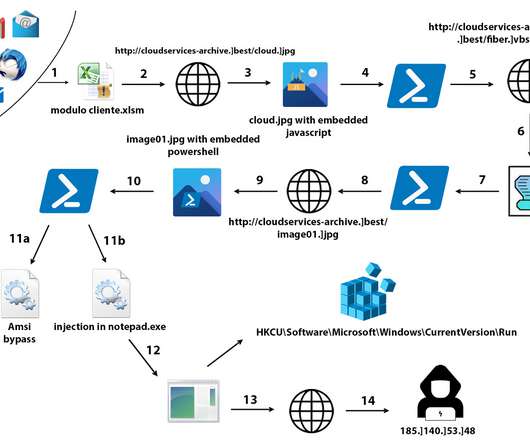
Threat actors were able to spread to other hosts through the use of USB drives, experts also noticed the deployment of a signed, but fake version of the application Zoom, which was a data stealing malware. “The archive contains two malicious DLL libraries as well as two legitimate executables that sideload the DLL files.













Let's personalize your content