A step-by-step guide to setting up a data governance program
IBM Big Data Hub
FEBRUARY 9, 2023
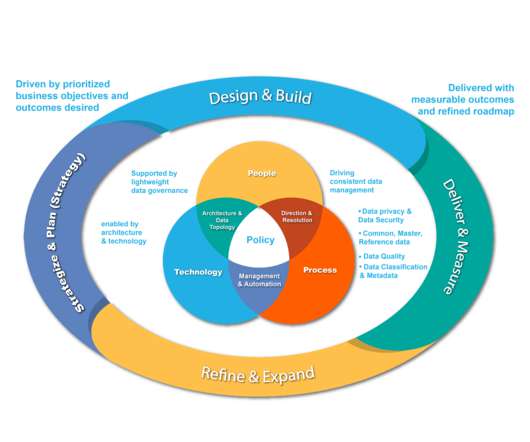
In our last blog , we delved into the seven most prevalent data challenges that can be addressed with effective data governance. Today we will share our approach to developing a data governance program to drive data transformation and fuel a data-driven culture.













Let's personalize your content