How to Prevent Malware Attacks: 8 Tips for 2023
IT Governance
APRIL 5, 2023
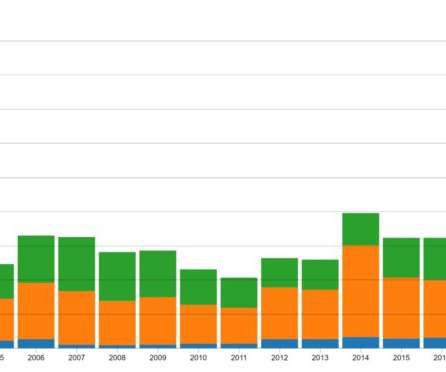
Malware is one of the most common cyber security threats that organisations and individuals face. Malware, or malicious software, is a broad term that refers to any type of code that intends to harm a computer. It’s why anti-malware software is usually considered a top priority for staying safe online. What is malware?

























Let's personalize your content