Breach Exposes Users of Microleaves Proxy Service
Krebs on Security
JULY 28, 2022
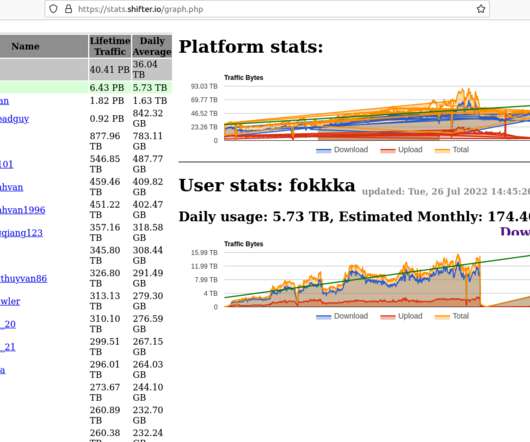
Microleaves , a ten-year-old proxy service that lets customers route their web traffic through millions of Microsoft Windows computers, recently fixed a vulnerability in their website that exposed their entire user database. By November 2013, Acidut was advertising the sale of “26 million SOCKS residential proxies.”














Let's personalize your content