More than 460,000 payment card details offered for sale on a black market
Security Affairs
DECEMBER 11, 2019
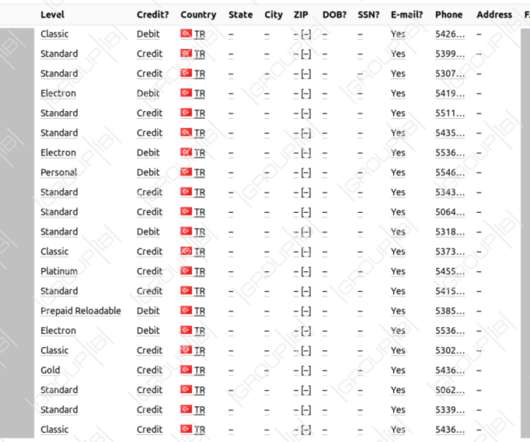
More than 455,000 Turkish payment card details are available for sale on a popular forum. Upon discovery of this database, Group-IB has informed proper local authorities about the sale of the payment records, so they could take necessary steps. More than 460,000 records in total were uploaded between Oct. 28 and Nov.














Let's personalize your content