PseudoManuscrypt, a mysterious massive cyber espionage campaign
Security Affairs
DECEMBER 16, 2021
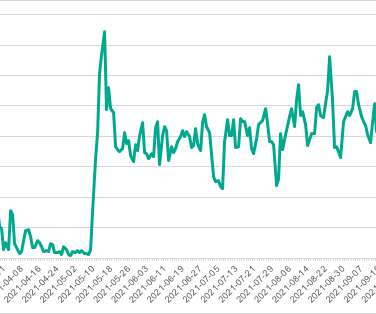
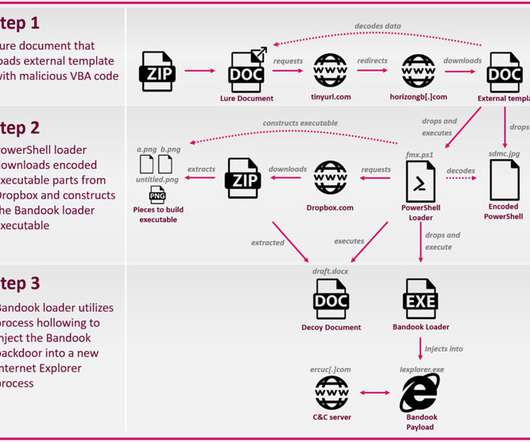
Kaspersky researchers reported that tens of thousands of devices belonging to industrial and government organizations worldwide have been hit by the PseudoManuscrypt spyware. The researchers also noticed that the malware samples also contain comments written in Chinese and that the spyware connects to the Baidu cloud storage service.














Let's personalize your content