Illegal Content and the Blockchain
Schneier on Security
MARCH 17, 2021
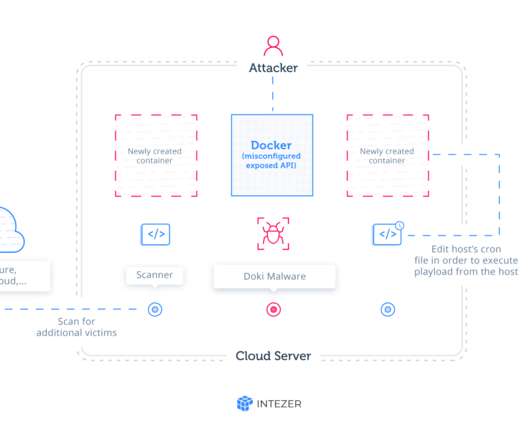
Security researchers have recently discovered a botnet with a novel defense against takedowns. Now the content-delivery network Akamai has reported on a new method: a botnet that uses the Bitcoin blockchain ledger. Now the content-delivery network Akamai has reported on a new method: a botnet that uses the Bitcoin blockchain ledger.


















Let's personalize your content