Lemon Group gang pre-infected 9 million Android devices for fraudulent activities
Security Affairs
MAY 19, 2023
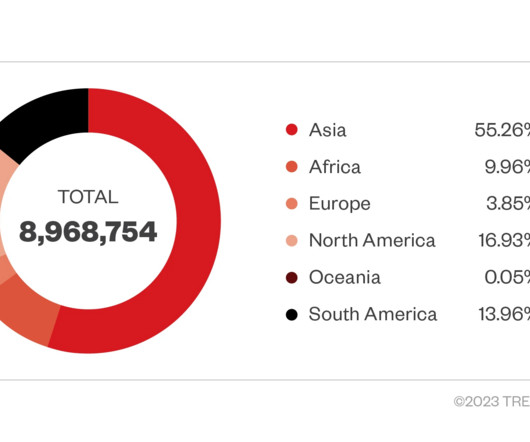
In March 2018, security researchers at Antivirus firm Dr. Web discovered that 42 models of low-cost Android smartphones are shipped with the Android.Triada.231 Soon after the security firm published a report on the group, the gang rebranded under the name ‘Durian Cloud SMS’, but maintained the C2 infrastructure.













Let's personalize your content