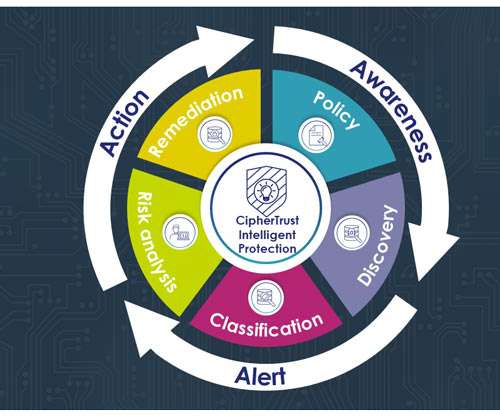
Don't Encrypt Everything; Protect Intelligently
Thales Cloud Protection & Licensing
NOVEMBER 11, 2021
Don't Encrypt Everything; Protect Intelligently. The volume of confidential documents created daily is, frankly, incalculable, and the volume of “everything” distributed across multiple data centers around the world is much, much more. Encrypting everything is time intensive because of explosive data growth.















Let's personalize your content