SolarWinds hackers stole some of Mimecast source code
Security Affairs
MARCH 17, 2021
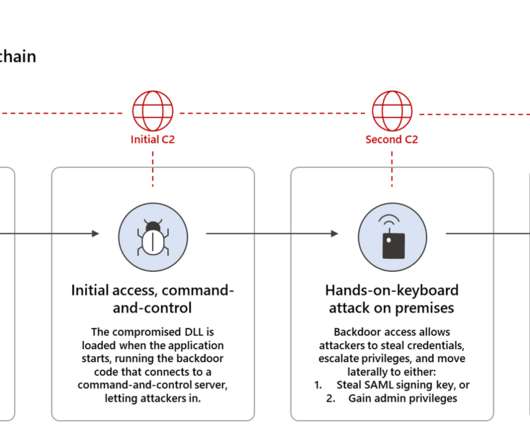
Back in December, the SolarWinds supply chain attack made the headlines when a Russian cyber espionage group tampered with updates for SolarWinds’ Orion Network Management products that the IT company provides to government agencies, military, and intelligence offices. ” reads the incident report published by mimecast.













Let's personalize your content