Threat actors found a way to bypass mitigation F5 BIG-IP CVE-2020-5902 flaw
Security Affairs
JULY 8, 2020
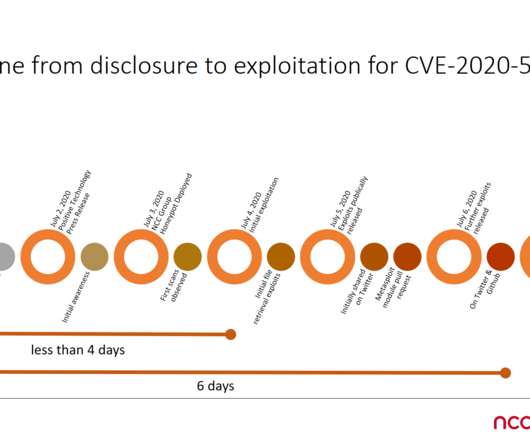
Unfortunately, threat actors in the wild were already using the bypass technique before its public disclosure. The BIG-IP product is an application delivery controller (ADC), it is used by government agencies and major business, including banks, services providers and IT giants like Facebook, Microsoft and Oracle.













Let's personalize your content