TA505 is expanding its operations
Security Affairs
MAY 29, 2019
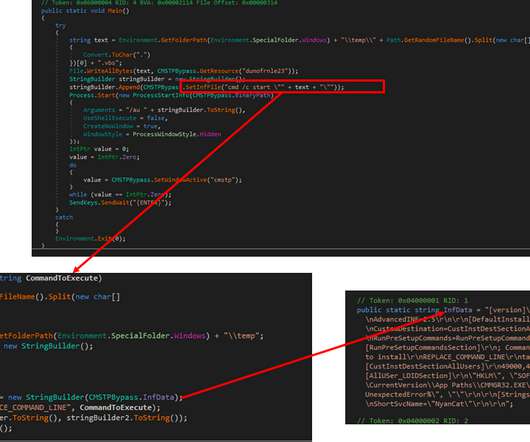
The threat group is also known for its recent attack campaign against Bank and Retail business sectors, but the latest evidence indicates a potential expansion of its criminal operation to other industries too. Technical Analysis. The tool is able to grant remote access and full, direct control of the infected machine to the group.


















Let's personalize your content