Phishing campaign targets LATAM e-commerce users with Chaes Malware
Security Affairs
NOVEMBER 18, 2020
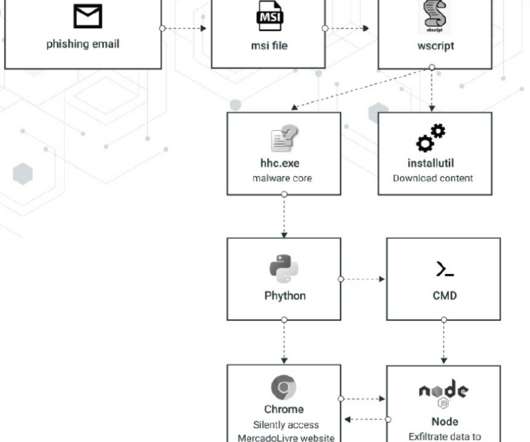
” reads the analysis published by Cybereason. The kill chain starts with phishing messages that use a.docx file that once is opened triggers a template injection attack. Experts observed several variants over the recent months, it authors have improved encryption and implemented new functionality of the final Node.js



























Let's personalize your content