Iranian hackers access unsecured HMI at Israeli Water Facility
Security Affairs
DECEMBER 4, 2020
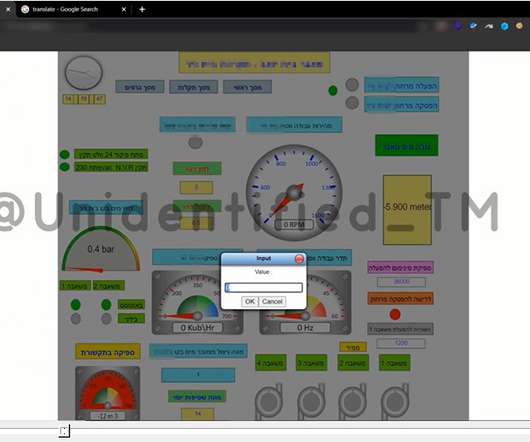
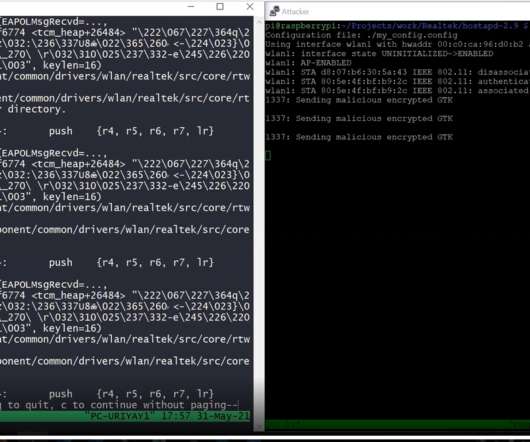
A group of Iranian hackers gained access to a un unprotected ICS at an Israeli Water Facility and posted a video as proof of the hack. The threat actors accessed a human-machine interface (HMI) system that was left unsecured online and published a video hack. ” reads the blog post published by OTORIO. Pierluigi Paganini.












Let's personalize your content