FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked
Krebs on Security
DECEMBER 13, 2022
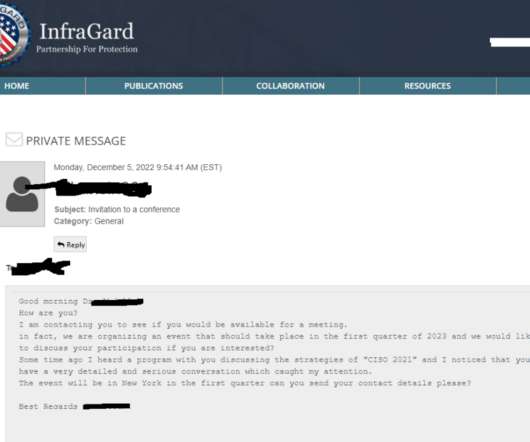
“InfraGard connects critical infrastructure owners, operators, and stakeholders with the FBI to provide education, networking, and information-sharing on security threats and risks,” the FBI’s InfraGard fact sheet reads. . That InfraGard member, who is head of security at a major U.S. Department of Defense.













Let's personalize your content