News alert: Silence Laboratories raises $4.1M for new privacy-preserving cryptography platform
The Last Watchdog
FEBRUARY 29, 2024
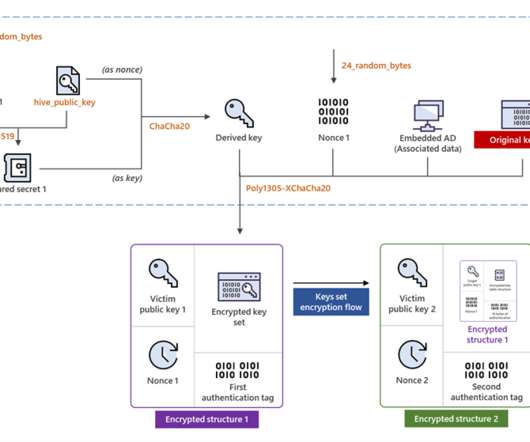
Leveraging modern cryptography, the company already has one of the fastest distributed signature (authorization) libraries in production ( Silent Shard ), which has been audited by some of the best security auditing companies like Trail of Bits. Privacy-preserving infrastructure combined with blockchain and fintech rails is going to be huge!”
















Let's personalize your content