US Cyber Command warns of Iran-linked hackers exploiting CVE-2017-11774 Outlook flaw
Security Affairs
JULY 2, 2019
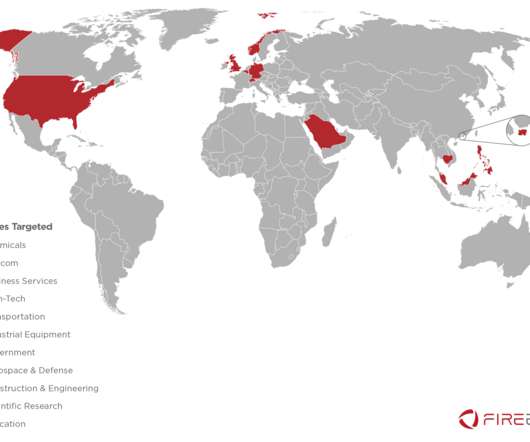
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production. These executables are both downloaders that utilize powershell to load the PUPY RAT. Most of the targets were in the Middle East, others were in the U.S.,













Let's personalize your content