Deadglyph, a very sophisticated and unknown backdoor targets the Middle East
Security Affairs
SEPTEMBER 24, 2023
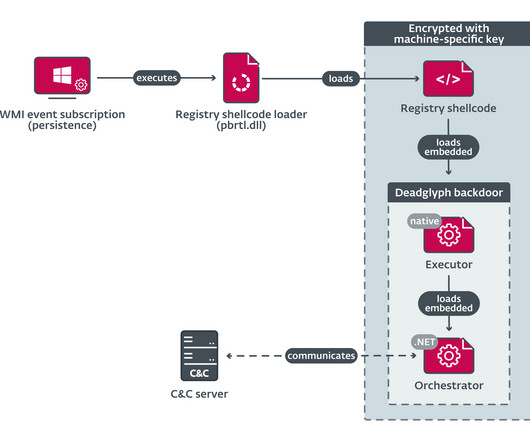
In 2016, researchers from the non-profit organization CitizenLab published a report that describes a campaign of targeted spyware attacks carried out by the Stealth Falcon. The authors used different languages to hinder analysis, researchers explained. ” reads the analysis published by ESET.



















Let's personalize your content