Qbot uses a new email collector module in the latest campaign
Security Affairs
AUGUST 31, 2020
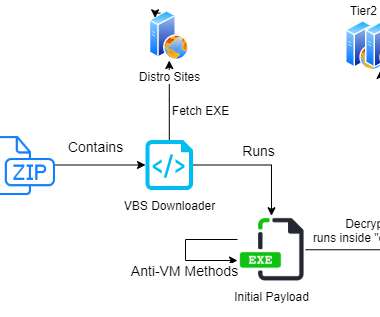
Most of the infections were observed in organizations in the US and Europe, the most targeted industries were in the government, military, and manufacturing sectors. . ” The spam messages contain URLs to.ZIP files that serve VBS content designed to download the payload from one of six hardcoded encrypted URLs. . .













Let's personalize your content