Devices from Dell, HP, and Lenovo used outdated OpenSSL versions
Security Affairs
NOVEMBER 25, 2022
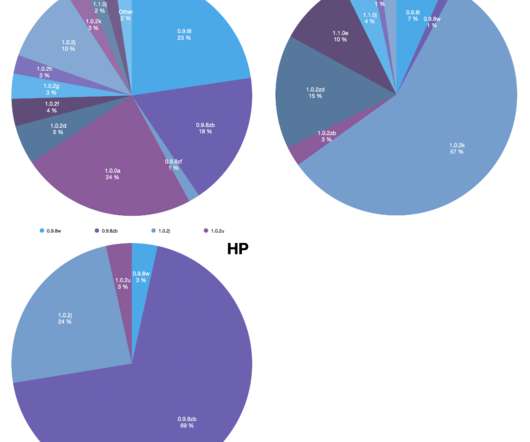
Researchers discovered that devices from Dell, HP, and Lenovo are still using outdated versions of the OpenSSL cryptographic library. Binarly researchers discovered that devices from Dell, HP, and Lenovo are still using outdated versions of the OpenSSL cryptographic library. ” continues the report. that dates back to 2009.













Let's personalize your content