MY TAKE: Why DDoS weapons will proliferate with the expansion of IoT and the coming of 5G
The Last Watchdog
MARCH 28, 2019
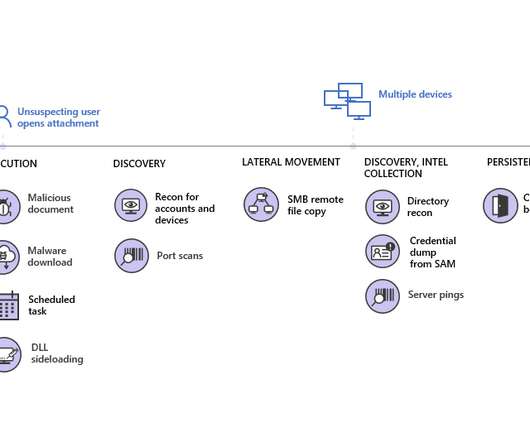
In March 2013, several impossibly massive waves of nuisance requests – peaking as high as 300 gigabytes per second— swamped Spamhaus , knocking the anti-spam organization off line for extended periods. This attacker easily located IoT devices that used the manufacturers’ default security setting.















Let's personalize your content