Updates from the MaaS: new threats delivered through NullMixer
Security Affairs
MARCH 27, 2023
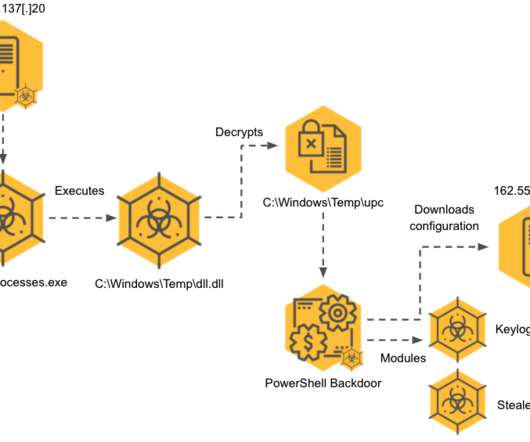
The threat actor abused Bitly shortener and an ad hoc BlogSpot account to protect the malicious code, lastly stored in an encrypted zip archive hosted on Mega.nz. Sqlcmd.exe, an interesting information stealer and dropper leveraging custom ECC cryptography to secure its communication (details below) KiffAppE2.exe,













Let's personalize your content