Lazarus malware delivered to South Korean users via supply chain attacks
Security Affairs
NOVEMBER 16, 2020
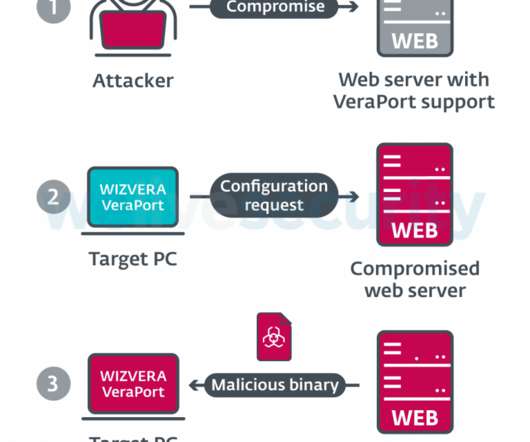
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. that is requested to visit particular government and banking domains.














Let's personalize your content