China-linked Winnti APT steals intellectual property from companies worldwide
Security Affairs
MAY 4, 2022
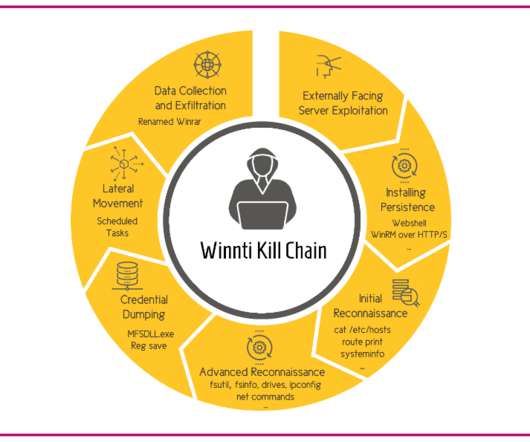
The campaign flew under the radar since at least 2019, it was attributed by the experts to the China-linked Winnti group and targeted technology and manufacturing companies primarily located in East Asia, Western Europe, and North America. ” reads the report published by Cybereason. The technique was rarely seen in attacks.












Let's personalize your content