Red Flags for Phishing: Verizon Outlines Common Scams to Watch Out For
KnowBe4
JANUARY 9, 2024
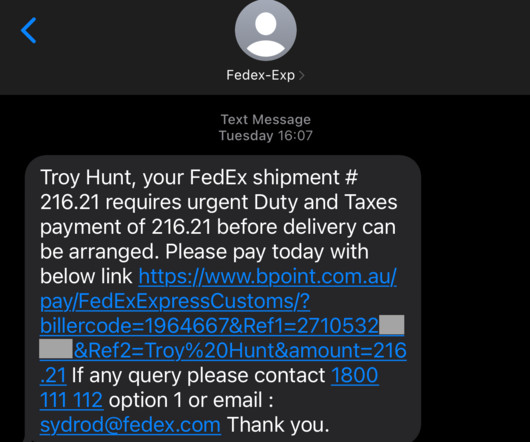
Verizon has published an article outlining various forms of social engineering attacks, including SMS/text messaging phishing (smishing), voice phishing (vishing), and spear phishing (targeted attacks, often via email). Verizon warns users to be on the lookout for the following red flags:

















Let's personalize your content