The Week in Cyber Security and Data Privacy: 5 – 11 February 2024
IT Governance
FEBRUARY 14, 2024
Subscribe now The post The Week in Cyber Security and Data Privacy: 5 – 11 February 2024 appeared first on IT Governance UK Blog.

IT Governance
FEBRUARY 14, 2024
Subscribe now The post The Week in Cyber Security and Data Privacy: 5 – 11 February 2024 appeared first on IT Governance UK Blog.

Security Affairs
JANUARY 26, 2020
of the Privacy Framework. Malware attack took down 600 computers at Volusia County Public Library. OP Glowing Symphony – How US military claims to have disrupted ISIS ‘s propaganda. NIST releases version 1.0 The Mystery of Fbot. US-based childrens clothing maker Hanna Andersson discloses a data breach.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
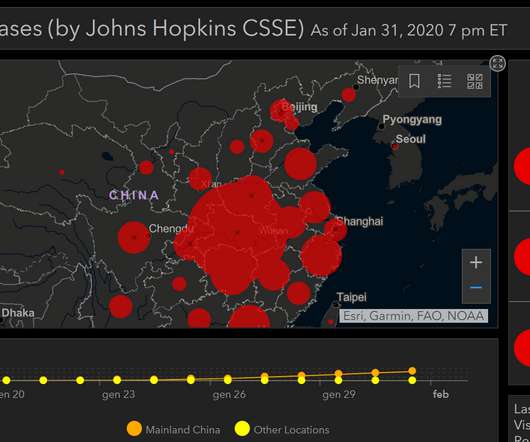
Security Affairs
FEBRUARY 2, 2020
A new piece of Ryuk Stealer targets government, military and finance sectors. Privacy watchdog opens an investigation. CVE-2020-7247 RCE flaw in OpenSMTPD library affects many BSD and Linux distros. Authorities arrest 3 Indonesian hackers behind many Magecart attacks. City of Potsdam offline following a cyberattack. Magento 2.3.4

The Security Ledger
JULY 26, 2018
» Related Stories Expert says: Hack your Smart Home to Secure It Fitness apps: Good for your health, not so much for military security Mobile, automation-industry leaders promote two new IoT security efforts. We have those libraries and we’ve wrapped our heads around how that works. Among them: establishing strong device.

Hunton Privacy
MAY 1, 2012
The proponents of the bill claimed that some of the amendments were aimed at addressing these privacy concerns. Under the proposed draft bill, there was no requirement to shield any personally identifying information that may be included in the cyber threat information. Federal Information Security Amendments Act.

Cyber Info Veritas
JULY 11, 2018
How VPNs work The role of a VPN is privacy: it allows you absolute privacy as you send data over a network. The first thing a VPN does to protect your privacy is to ensure that your internet service provider does not access your information or, at the very least, your ISP does not keep a copy of your log.

ForAllSecure
MAY 17, 2023
It's not just going to be Taiwan, they're going to be facing as for example, in this case, you know, the United States has come straight out and said they are our military ally. You're taking non military people large amounts of skill, you're politicizing and enabling that as a weapon of war. China invaded Taiwan. That's a big step.
Let's personalize your content