Rhysida ransomware gang is auctioning data stolen from the British Library
Security Affairs
NOVEMBER 20, 2023
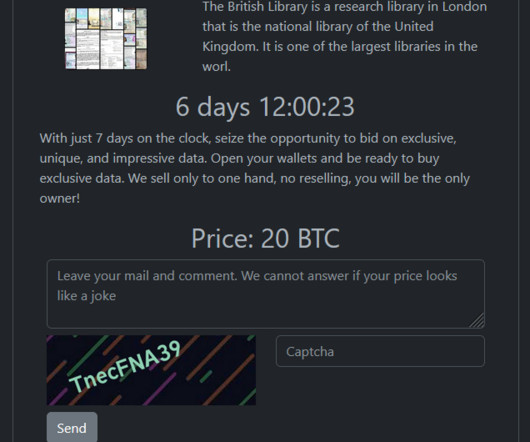
The Rhysida ransomware group claimed responsibility for the recent cyberattack on the British Library that has caused a major IT outage. The Rhysida ransomware gang added the British Library to the list of victims on its Tor leak site. It is one of the largest libraries in the world. ” reads the announcement.


















Let's personalize your content