Million of vehicles can be attacked via MiCODUS MV720 GPS Trackers
Security Affairs
JULY 20, 2022
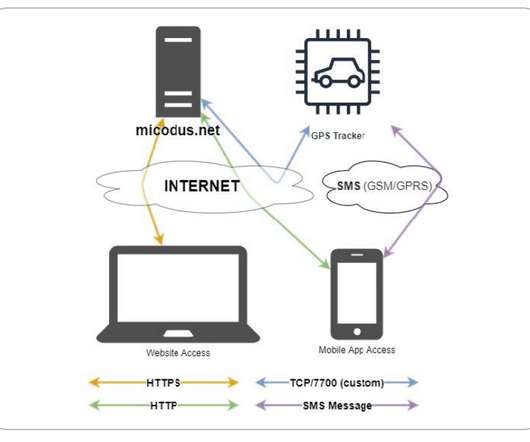
Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to warn of multiple security vulnerabilities in MiCODUS MV720 Global Positioning System (GPS) trackers which are used by over 1.5 Multiple flaws in MiCODUS MV720 Global Positioning System (GPS) trackers shipped with over 1.5 million vehicles.












Let's personalize your content