Targeted operation against Ukraine exploited 7-year-old MS Office bug
Security Affairs
APRIL 28, 2024
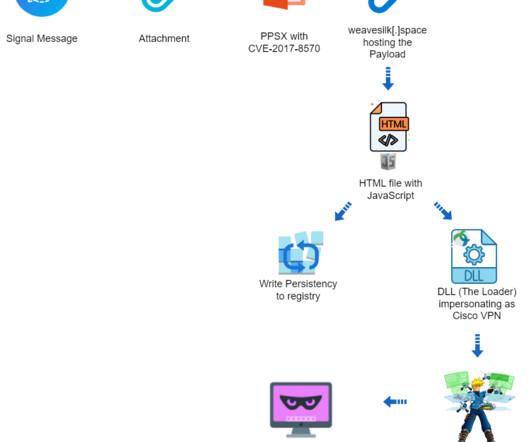
It’s a PPSX file, seemingly an outdated US Army manual for tank mine clearing blades (MCB). The payload includes a dynamic-link library (vpn.sessings) that injects the post-exploitation tool Cobalt Strike Beacon into memory and awaits commands from the C2 server. The PPSX file contains a remote link to an external OLE object.














Let's personalize your content