15 billion credentials available in the cybercrime marketplaces
Security Affairs
JULY 9, 2020
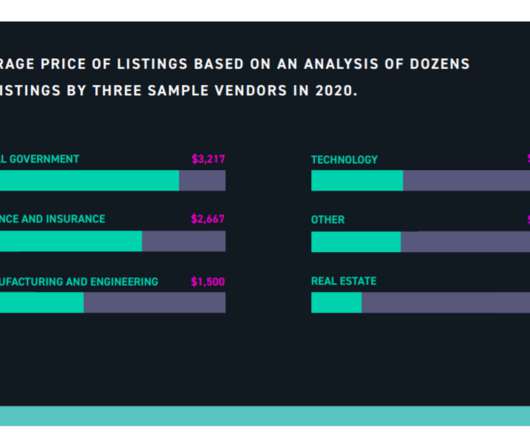
A report published by security firm Digital Shadows r evealed the availability of more than 15 billion credentials shared on cybercrime marketplaces, paste sites, file sharing services, and code sharing websites. Using the recently launched model of ATO “as-a-service”, a criminal can rent an identity for less than $10.













Let's personalize your content