Atlassian Confluence bug CVE-2022-26134 exploited in cryptocurrency mining campaign
Security Affairs
SEPTEMBER 22, 2022
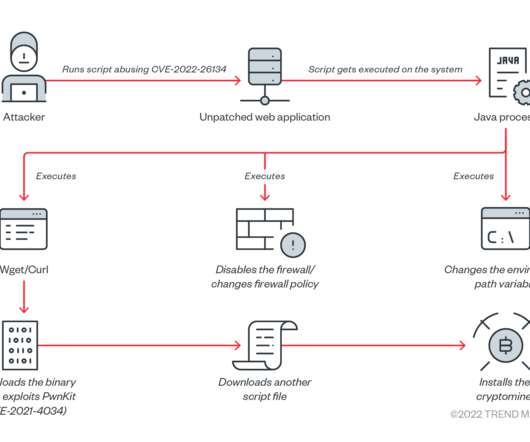
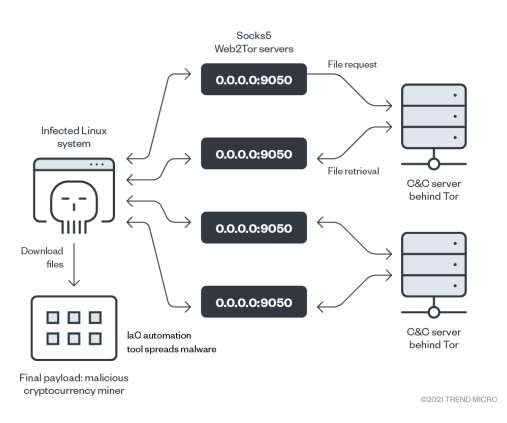
Threat actors are targeting unpatched Atlassian Confluence servers as part of an ongoing crypto mining campaign. Trend Micro researchers warn of an ongoing crypto mining campaign targeting Atlassian Confluence servers affected by the CVE-2022-26134 vulnerability. in the collaboration tool Atlassian Confluence. .











Let's personalize your content