Experts attribute WyrmSpy and DragonEgg spyware to the Chinese APT41 group
Security Affairs
JULY 20, 2023
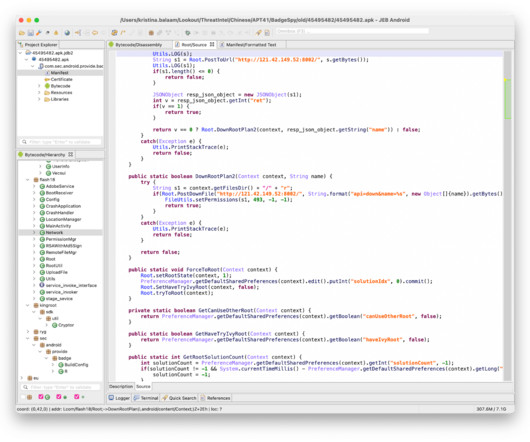
government. Later variants masquerade as adult video content, “Baidu Waimai” food delivery platform, and Adobe Flash. “It then receives a response containing a file name which the malware uses to download additional rooting binaries from C2 infrastructure if one exists for the specified device.”














Let's personalize your content