Sending Spammers to Password Purgatory with Microsoft Power Automate and Cloudflare Workers KV
Troy Hunt
AUGUST 3, 2022
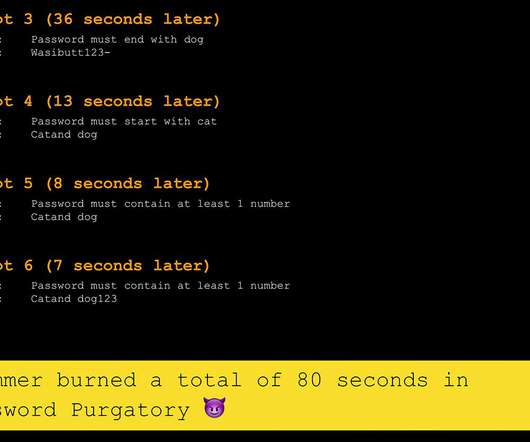
So, earlier this year I created Password Purgatory with the singular goal of putting spammers through the hellscape that is attempting to satisfy really nasty password complexity criteria. I opened-sourced it, took a bunch of PRs, built out the API to present increasingly inane password complexity criteria then left it at that.


















Let's personalize your content