Counting Down to the EU NIS2 Directive
Thales Cloud Protection & Licensing
MAY 22, 2024
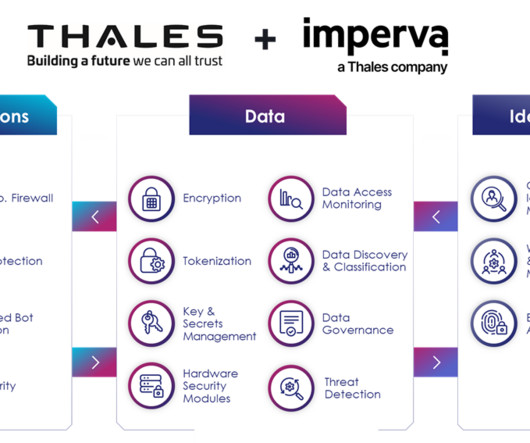
NIS2 expands the original NIS Directive to cover more industry sectors, with additional risk-management measures and incident reporting obligations. NIS2 adds digital service providers, waste management, pharmaceutical and labs, space, and public administration to the ‘Essential’ sectors category. Cryptography and encryption.













Let's personalize your content