Night Sky ransomware operators exploit Log4Shell to target hack VMware Horizon servers
Security Affairs
JANUARY 11, 2022
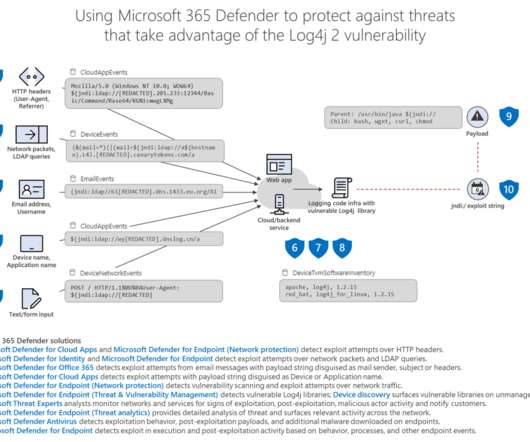
Another gang, Night Sky ransomware operation, started exploiting the Log4Shell vulnerability in the Log4j library to gain access to VMware Horizon systems. The Night Sky ransomware operation started exploiting the Log4Shell flaw (CVE-2021-44228) in the Log4j library to gain access to VMware Horizon systems. trendmrcio[.]com,



















Let's personalize your content