In High Demand - How Thales and DigiCert Protect Against Software Supply Chain Attacks
Thales Cloud Protection & Licensing
APRIL 15, 2024
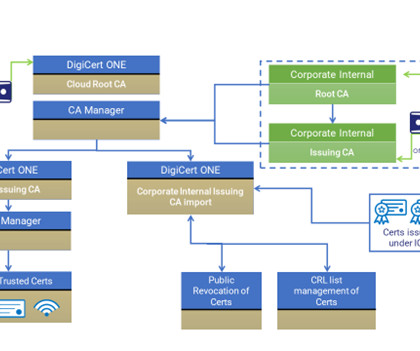
The news has already captured some very high-profile incidents, including attacks on an American retailer, a software vendor, and more recently a multinational investment and financial services bank. Examples include covertly inserting malware or manipulating unprotected code-signing keys. How are the hackers getting in?














Let's personalize your content