Threat actors found a way to bypass mitigation F5 BIG-IP CVE-2020-5902 flaw
Security Affairs
JULY 8, 2020
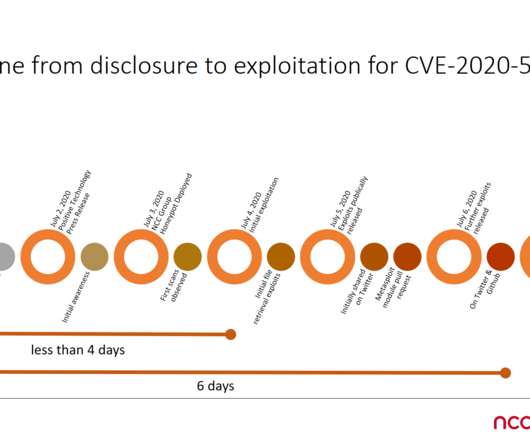
Unfortunately, threat actors in the wild were already using the bypass technique before its public disclosure. A few days after the disclosure of the vulnerability in the F5 Networks BIG-IP product threat actors started exploiting it in attacks in the wild. remote code execution vulnerability in the Big-IP administrative interface. .”














Let's personalize your content