Iran-linked Mint Sandstorm APT targeted US critical infrastructure
Security Affairs
APRIL 19, 2023
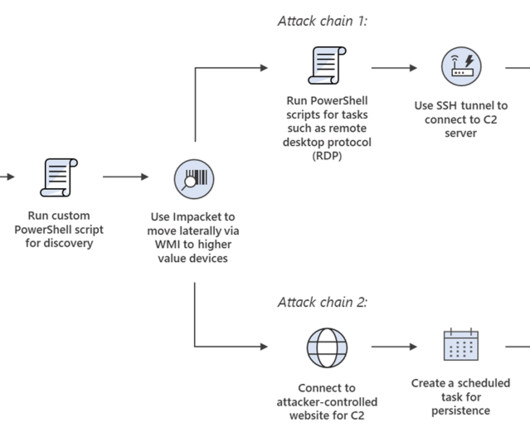
“Microsoft assesses that Mint Sandstorm is associated with an intelligence arm of Iran’s military, the Islamic Revolutionary Guard Corps (IRGC), an assessment that has been corroborated by multiple credible sources including Mandiant , Proofpoint , and SecureWorks.” ” reads the report published by Microsoft.



















Let's personalize your content