US Agencies and FireEye were hacked with a supply chain attack on SolarWinds Software
Security Affairs
DECEMBER 14, 2020
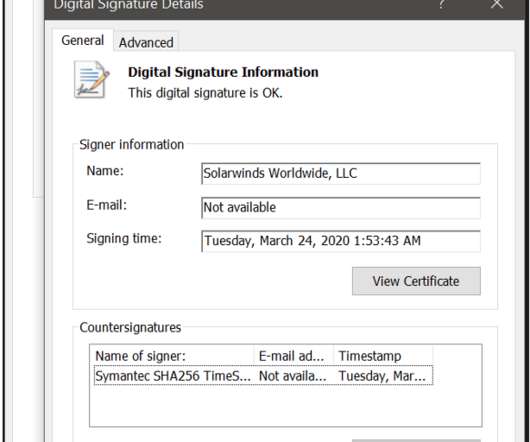
The cyber espionage group has tampered with updates released by IT company SolarWinds, which provides its products to government agencies, military, and intelligence offices, two people familiar with the matter told the Reuters agency. . ” reported the Reuters. Threat actors carried out a highly-sophisticated supply chain attack.


















Let's personalize your content