Authorities arrest 3 Indonesian hackers behind many Magecart attacks
Security Affairs
JANUARY 26, 2020
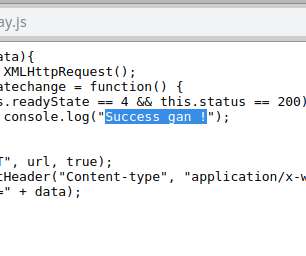
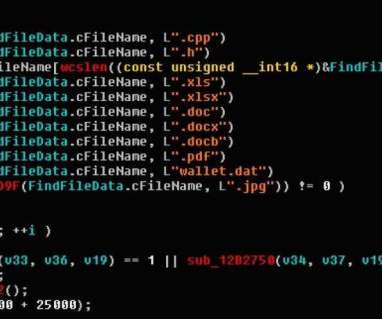
The Indonesian National Police and the Interpol announced the arrest of three Indonesian hackers who carried out Magecart attacks. The Indonesian National Police in a joint press conference with Interpol announced the result of an investigation dubbed ‘Operation Night Fury’ that allowed to arrest three hackers that carried out Magecart attacks to steal payment card data.














Let's personalize your content