Microsoft's June Patch Tuesday Covers Very Exploitable Bugs
Data Breach Today
JUNE 14, 2023
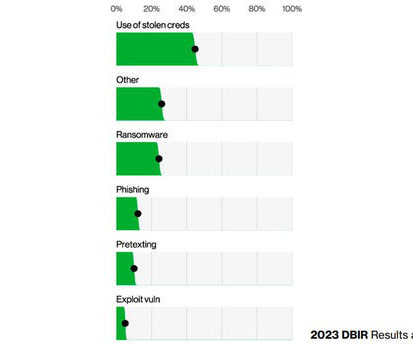
SharePoint, Multicasting and Exchange Figure Prominently This Month Microsoft's June dump of monthly patches for the first time in months doesn't include a fix for an actively exploited zero day in a slew of fixes for 69 vulnerabilities spread across the computing giant's portfolio of products. Among them: SharePoint, Exchange and serves that enable multicasting.





































Let's personalize your content