US-based children’s clothing maker Hanna Andersson discloses a data breach
Security Affairs
JANUARY 21, 2020
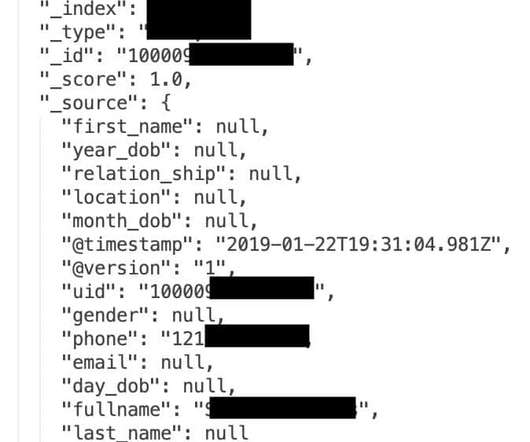
The US-based children’s clothing maker Hanna Andersson has disclosed a data breach that affected its customers. The US-based children’s clothing maker and online retailer Hanna Andersson discloses a data breach, attackers planted an e-skimmer on its e-commerce platform. Hannah Anderson was breached.














Let's personalize your content