How to Prevent Web Attacks Using Input Sanitization
eSecurity Planet
APRIL 13, 2022
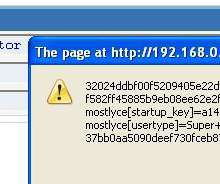
Despite all the security measures you might take, a codebase can be the weakest link for any business’s cybersecurity. Sanitizing consists of removing any unsafe character from user inputs, and validating will check if the data is in the expected format and type. Sanitizing and validating inputs is usually the first layer of defense.













Let's personalize your content