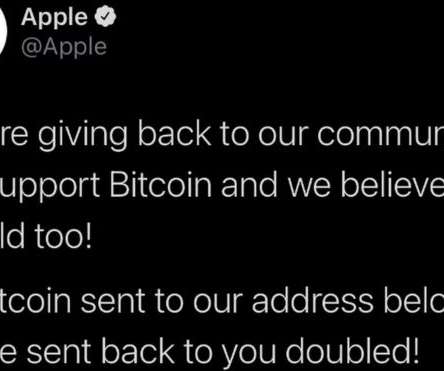
Four individuals charged for the recent Twitter hack
Security Affairs
AUGUST 1, 2020
. “The charges he’s facing include one count of organized fraud, 17 counts of communications fraud, one count of fraudulent use of personal information with over $100,000 or 30 or more victims, 10 counts of fraudulent use of personal information and one count of access to computer or electronic device without authority.”



















Let's personalize your content