Evilnum APT used Python-based RAT PyVil in recent attacks
Security Affairs
SEPTEMBER 3, 2020
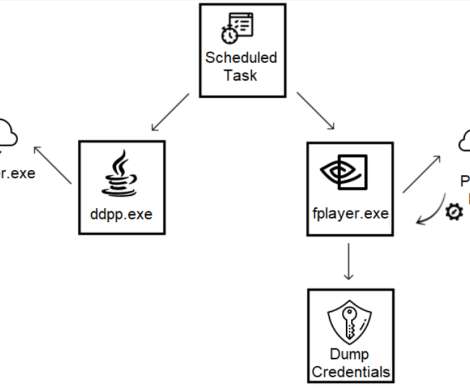
The malware communicates with the C2 communications via POST HTTP requests and uses RC4 encryption with a hardcoded key encoded with Base64. When the LNK file is executed, a JavaScript file is called, which acts only as a first-stage dropper (the file name is ddpp.exe).










Let's personalize your content