China-linked LuminousMoth APT targets entities from Southeast Asia
Security Affairs
JULY 14, 2021
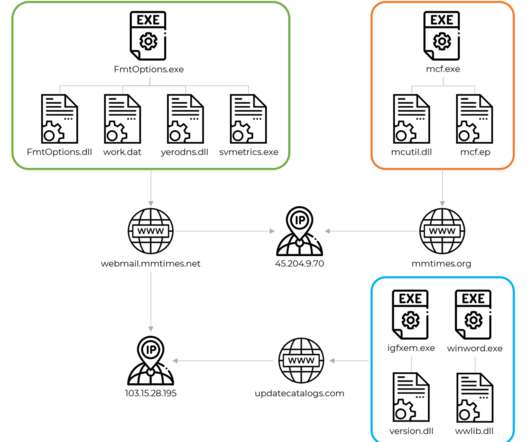
. “The archive contains two malicious DLL libraries as well as two legitimate executables that sideload the DLL files. We found multiple archives like this with file names of government entities in Myanmar, for example “COVID-19 Case 12-11-2020(MOTC).rar” ” reads the analysis published by Kaspersky.














Let's personalize your content