The risk of pasting confidential company data into ChatGPT
Security Affairs
MARCH 12, 2023
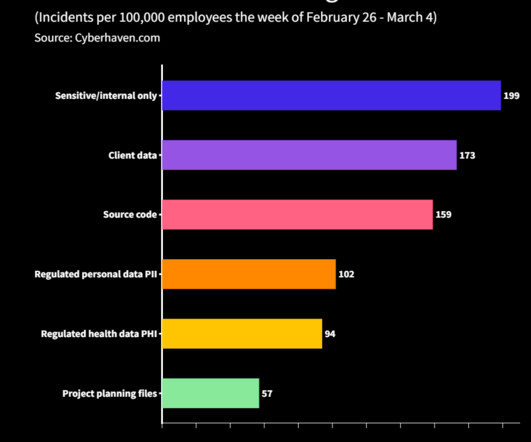
ChatGPT uses this data to build its knowledge base, but it publicly shares information built on it. This percentage could rapidly increase in the next months with the integration of the technology in multiple services, for example through the use of ChatGPT API. They reported that 5.6%













Let's personalize your content