New AlienFox toolkit harvests credentials for tens of cloud services
Security Affairs
MARCH 30, 2023
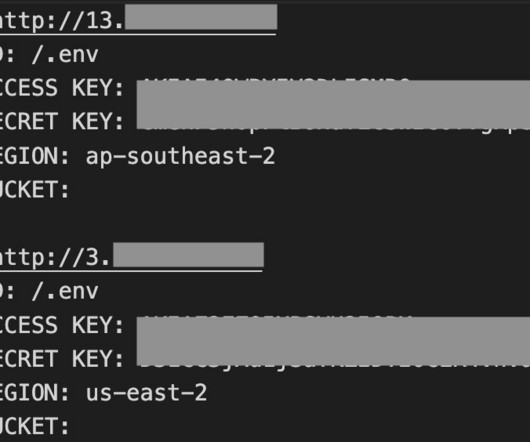
AlienFox is a novel comprehensive toolset for harvesting credentials for multiple cloud service providers, SentinelLabs reported. AlienFox is a new modular toolkit that allows threat actors to harvest credentials for multiple cloud service providers. Many developers take credit on different iterations of the tools.”

















Let's personalize your content